Last updated on November 16th, 2022 at 03:48 pm
As companies grow, so do the needs of users or departments. Today, data or network security is in the spotlight and becoming more frontline. One of the many security features of firewalls, which has expanded with the Next Generation Firewall, is User Identification (User ID) and using this information for securing access. This security feature is especially useful when user resources are in many places like the data center (DC), disaster recovery DC, the cloud, and the same location as the user.
The user ID can be a username, most likely an Active Directory (AD) username, for example, jwick. It can also be an AD group in which a user is a member. Either way, an AD username or group can be used on the firewall to access a network or specific host.
This article will review the redistribution of User-ID information obtained from GlobalProtect VPN connections and the Palo Alto Networks (PAN) Windows User-ID Agent to Panorama. User-ID redistribution can be done without Panorama, but in at least medium to a large companies (and some small), Panorama is common and makes an excellent central repository. This article uses Panorama as the central repository.
Note: PAN documentation version 10.0 and newer, User-ID redistribution is now generally categorized as Data Redistribution; see the Reference Links section at the end of this article.
The Infrastructure
Let’s review the infrastructure used in this article.
This infrastructure includes multiple PAN firewalls and a Panorama server. The four firewalls that send User-ID data to Panorama are Internet edge firewalls, and two are GlobalProtect Gateways. The fifth firewall, LasVegas-Office, will poll Panorama for User-ID information.
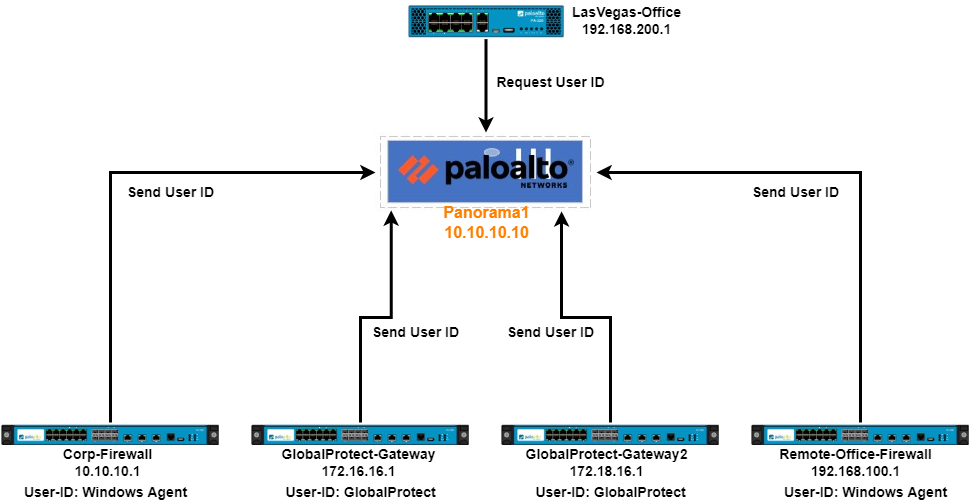
Two firewalls, Corp-Firewall and Remote-Office-Firewall, use the PAN Windows User-ID agent to map usernames to IP addresses. The other two firewalls are GlobalProtect Gateways and so, using these GP connections to map usernames to IP addresses. All four firewalls send the username to IP mapping to Panorama (Panorama1).
This article does not discuss the installation or configuration of the User-ID Agent, and here is a link to User-ID documentation. https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/user-id
Also, this article assumes GlobalProtect or the Windows Agent is installed, and the firewall is configured to use the Agent.
The Goal
The goal is to have User-ID information (username to IP mapping) centralized in Panorama. This allows firewalls to retrieve this information from Panorama, which can be used in, for example, Security Policies.
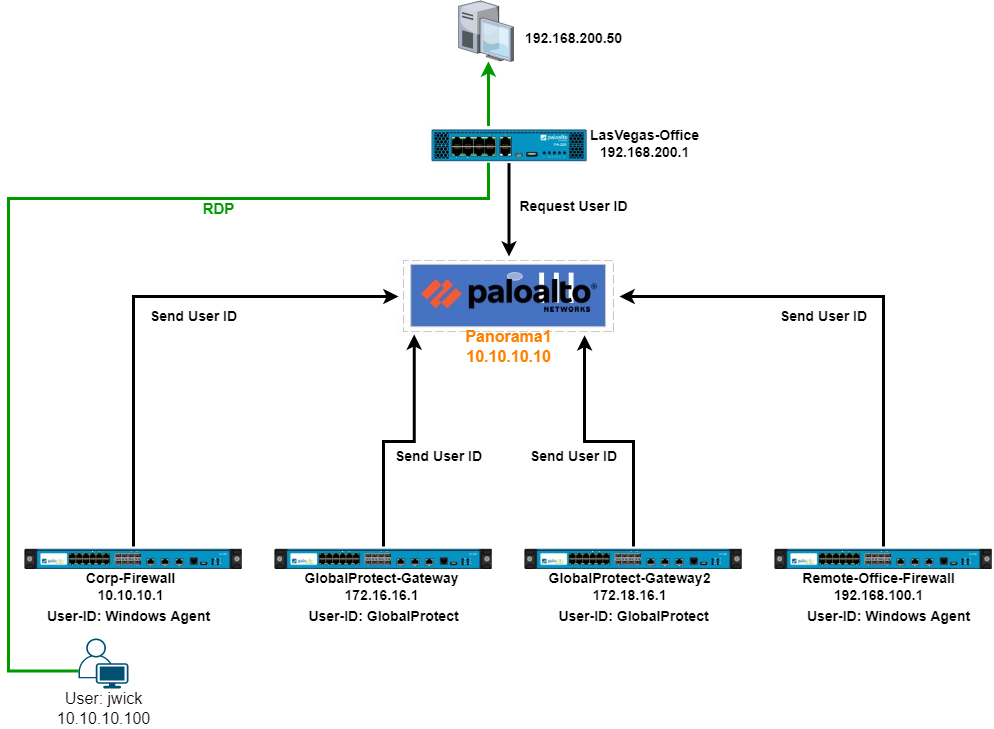
In this article, as an example, a user in the corporate office needs access to host 192.168.200.50 in the LasVegas-Office. On the LasVegas-Office firewall, we want to use a Security Policy that uses a username or group in the Source, and so this firewall needs to know the username and IP mapping.
Configure the User-ID Sending Firewalls
Note: In PAN documentation version 9.1 and older, User-ID redistribution is referred to as “User-ID Redistribution.” In version 10.0 and newer, it’s referred to as “Data Redistribution.” This article follows the 10.1 version of the documentation but included are configurations for 9.1 and 10.1.
Here we will configure the sending (redistribution) firewalls to send the username to IP address mapping data.
On the sending (Collector) firewall with version 9.1:
Go to Device>User Identification>User Mapping
Edit the Palo Alto Networks User-ID Agent Setup by clicking the cog wheel in the right corner.
On the Redistribution tab, name this collector (one option is the firewall’s name) and enter a pre-shared key (note this down as it will be used later in Panorama).
Then click OK.

On the sending (Collector) firewall with version 10.0 or later:
Go to Device>Data Redistribution>Collector Settings
To the right of Data Redistribution Agent Setup, in the right corner, click the cog wheel.
Name this collector (one option is the firewall’s name) and enter a pre-shared key (note this down as it will be used later in Panorama).
Then click OK.

Also, on 10.0 and later, as stated in the documentation, networks can be included or excluded for user IP mappings. This should be considered if the sending firewall has multiple networks and only IP mapping is needed from select networks. Also, if the firewall is a GlobalProtect VPN gateway, the GlobalProtect network can be defined.
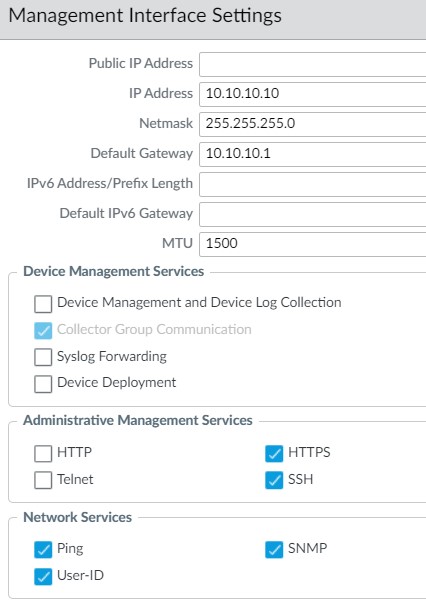
With either version, update the Management interface profile to support User-ID for redistribution.
Device>Setup>Interfaces click the Management interface. In the Network Services section, enable User-ID. After committing the configuration, repeat this step on the other (passive) firewall.

Commit the configuration.
Repeat these previous steps for each firewall sending User-ID data to Panorama.
Refer to the documentation to use the CLI to check or confirm User-ID information.
Configure Panorama to Sync with the Sending Firewalls
In this step, Panorama is running version 10.1.
We will configure Panorama to receive User-ID information from the firewalls.
In Panorama:
Go to Panorama>Data Redistribution> Agents
Click Add to add a new agent.
The Agent is the firewall(s) configured in the previous section and is the sending (Collector) firewall(s). In this topology, those are these four firewalls.
With this topology, the firewalls don’t have to fail over to the other if there is an ISP failure.

The Name field is a friendly name only in Panorama, and the Collectorname is the name used in the firewall configuration in the previous section, so in this example, Corp-firewall. The Name and Collectorname fields can be the same, but the Collectorname must match that configured on the firewall.
Enter the Management IP address of the sender firewall, so in this example, the Corp-Firewall Management IP address 10.10.10.1.
Be sure the port number is the same in Panorama and the sending firewall.
Enter the pre-shared key used on the firewall and used in the previous section.
In Data type, check IP User Mappings.

Repeat these steps for each firewall sending user ID data to Panorama.

Enable Panorama to respond to firewalls for user ID data redistribution.
Go to Panorama>Setup>Interfaces>Management
In the Network Services section, enable User-ID.
If Panorama is in HA, repeat these steps on the other Panorama server.
Commit the configuration to Panorama.
After the configuration is committed, check the communication status to each sending firewall.
Go to Panorama>Data Redistribution>Agents
At the bottom, click Agent Statistics. In the Status column, click Status to view the communication details with that firewall.
Also, in Panorama, check that User-ID data is being received.
Go to Monitor>Logs>User-ID

Configure the Non-Agent Firewall
Here we configure the LasVegas-Office firewall to use Panorama as a User-ID Agent.
Note: the configuration is slightly different for versions 9.1 and 10 and later.
With either PAN-OS version, there are two ways to add the Panorama servers as an Agent in the firewall.
The Panorama servers can be added via host IP address, port, and other information. The easiest and preferred method is by Serial Number.
If the firewall is managed by Panorama or at least in Panorama for summary/health monitoring, then the Serial Number method can be used and is the easiest. This article assumes the firewall is in Panorama.
Version 9.1
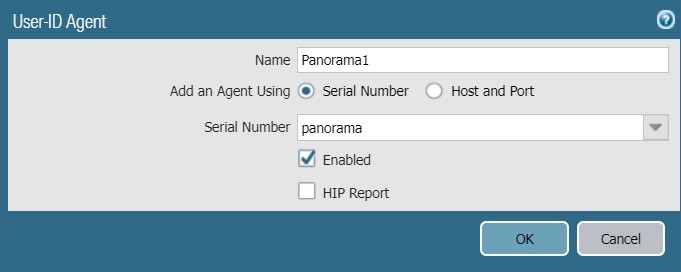
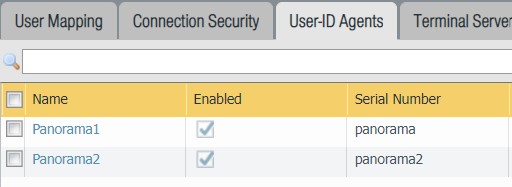
Go to Device>User Identification>User-ID Agents
Click Add
For Name, use the name of the primary Panorama server. In this article, that is Panorama1.
Confirm Serial Number is selected.
In the Serial Number drop-down, select panorama. The drop-down option of panorama and panorama2 come from the Panorama settings in Device>Setup>Management>Panorama Settings.
Confirm Enabled is checked.
If there is a second (passive) Panorama server, then repeat these steps for the second server, but this time in the Serial Number drop-down, select panorama2.
Click Ok.
Commit the configuration.
Version 10.0 or Later
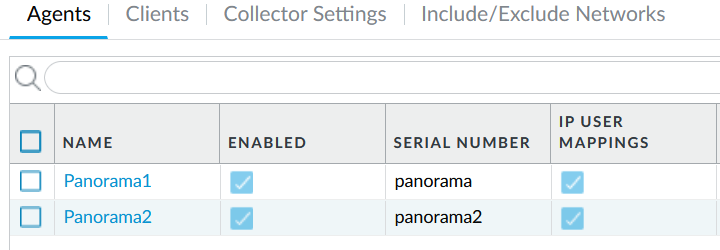
Device>Data Redistribution>Agents
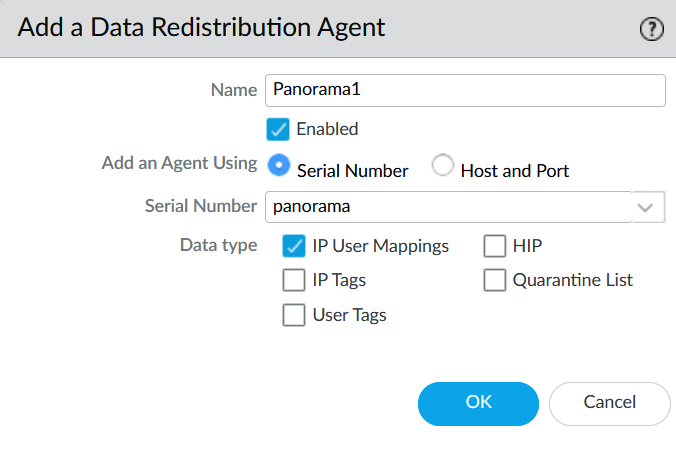
For Name, use the name of the primary Panorama server. In this article, that is Panorama1.
Confirm Enabled is checked.
Confirm Serial Number is selected.
In the Serial Number drop-down, select panorama. The drop-down option of panorama and panorama2 come from the Panorama settings in Device>Setup>Management>Panorama Settings.
In the Data type field, check IP User Mappings.
If there is a second (passive) Panorama server, then repeat these steps for the second server, but this time in the Serial Number drop-down, select panorama2.
Click Ok.
Commit the configuration.
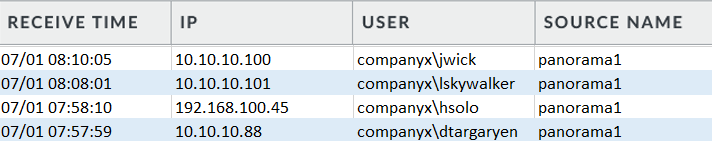
Once the configuration is committed, check the logs.
Go to Monitor>Logs>User-ID
This log should begin populating with information from the Panorama server.
Whew!
If all is configured correctly, then in our topology, the LasVegas-Office firewall should have User-ID info. At this time, this information can be used on the Las Vegas firewall in a Security Policy.
User jwick Needs RDP Access
Now, to use the fruits of our labor.
In this article’s example, user jwick needs to access host 192.168.200.50 in the Las Vegas office via RDP. One requirement in the Security Policy on the Las Vegas firewall is that either an AD username or group is used in the source field of the Security Policy.

In this example, the Las Vegas firewall Security policy, the Source User field has the user jwick as this user is located in the corporate office (Corp-Firewall). The Source User field can also use an AD group but requires LDAP configuration on the firewall.
When we look at the User-ID log on the Las Vegas firewall, we see user jwick maps to IP address 10.10.10.100 and received from the Panorama server we configured previously.

If all is configured properly and working, the user jwick should have RDP access to host 192.168.200.50.
Another option for the Security Policy in this example is to place the Security Policy with the source user on the Corp-Firewall. This can be reversed if, for example, a user in the Remote-Office-Firewall office needs access to resources behind the Corp-Firewall.
Conclusion
User-ID (Data) redistribution, with Panorama, is a great way of sharing this information with multiple devices. The ability to have this information across the organization’s geographical and cloud infrastructure, user ID should be used as another element in Security Policies, whether it be an AD username or group.
With work from home or hybrid working and using GlobalProtect VPNs, and resources in multiple locations, now is the time to use User-ID to secure access to resources.
Reference Links:
Copyright © Packet Passers 2025


