Last updated on November 16th, 2022 at 05:07 pm
Fortunately for us firewall Administrators or Engineers, Palo Alto Networks provides two external dynamic lists (EDL) for blocking or allowing traffic. PAN offers two types of EDLs, built-in and hosted, and a third is available for hosting your custom list. This one option, Minemeld, was supported by PAN-OS and a GitHub project and is the end of life. Many of the services in MineMeld have migrated to Cortex XSOAR and the EDL Hosting Service.
Built-in EDLs
The built-in has been around for a while and has grown over time, and as of PAN-OS version 9.1, the EDLs available are Bulletproof, High-Risk, Known Malicious, and Tor Exit IP address lists. These lists are commonly used for blocking inbound (if you host service) and outbound (see image) and updated with a Threat Prevention subscription.

Note that I had a couple of times when the High-Risk EDL blocked valid traffic. Fortunately, this is rare but still worth using this EDL for its security. If a valid IP address is blocked, the list has the option to move the address to the Manual Exceptions list (Palo Alto Networks – High risk IP addresses>List Entries and Exceptions tab).
EDL Hosting Service
The EDL Hosting Service is provided by Palo Alto Networks and is free. This service is usually used in an allow security policy, though it can be used in a deny policy. The EDL Hosting maintains the ever-dynamic list of IP addresses for (at the time of this post) Microsoft 365, Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP).
https://docs.paloaltonetworks.com/resources/edl-hosting-service.html
https://saasedl.paloaltonetworks.com/feeds.html
The EDL Hosting Service is beneficial when security policies are required and narrowed down to a specific service (SaaS). For example, for AWS S3 in the US East region. This was a significant challenge to maintain before the EDL Hosting Service and if you want to specify all AWS S3 IP addresses, for example.
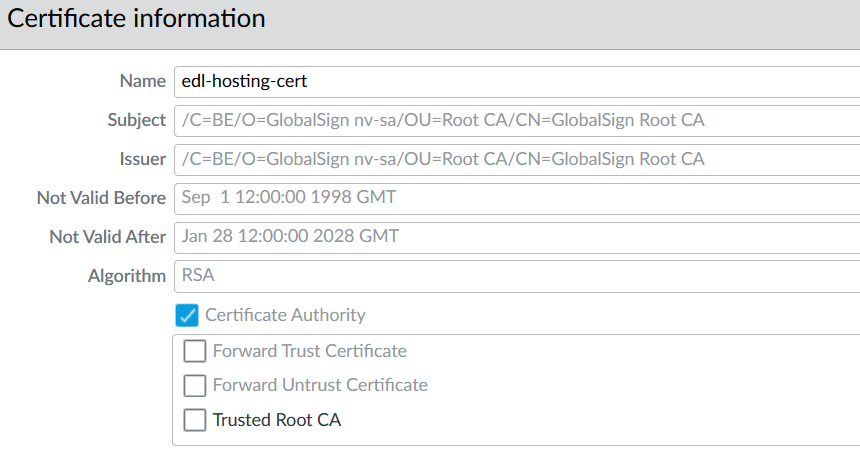
When I set up the EDL Hosting Service on a firewall, I followed the links below and in order. I highly recommend in the Create an External Dynamic List Using the EDL Hosting Service document to follow Step 2 of using a certificate and certificate profile for this service. Also, this document is very detailed and suitable for following a step-by-step process of creating an EDL using the hosting service.
- https://docs.paloaltonetworks.com/resources/edl-hosting-service.html
- https://saasedl.paloaltonetworks.com/feeds.html
- https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/policy/use-an-external-dynamic-list-in-policy/configure-the-firewall-to-access-an-external-dynamic-list-from-the-edl-hosting-service/create-an-external-dynamic-list-using-the-edl-hosting-service.html#idfd14e570-1fc3-488e-b574-fc42e84dd649
- https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/policy/use-an-external-dynamic-list-in-policy/enforce-policy-on-an-external-dynamic-list.html
Note that the built-in and EDL Hosting Service external dynamic lists cannot be nested in an Address Group.
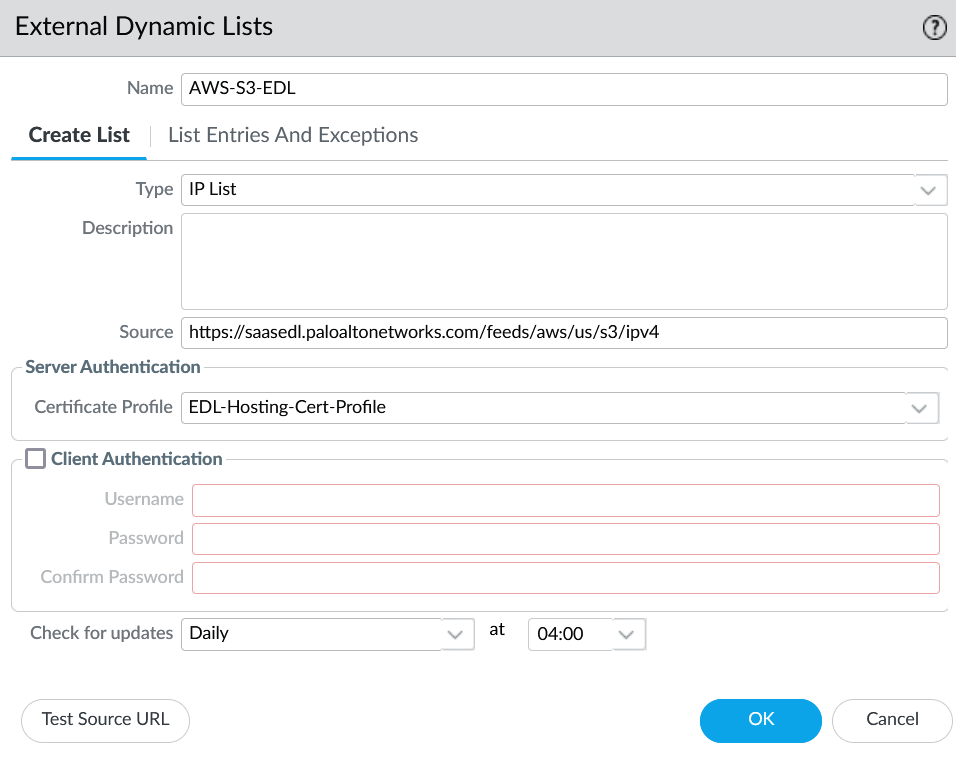
Here are screenshots of my configuration for all US IPv4 AWS S3 dynamic lists, which I used in a security policy allowing access from a specific source (172.16.20.5). These are based on the Create an External Dynamic List Using the EDL Hosting Service document.

When using the EDL Hosting Service, Client Authentication is not necessary, so you can ignore the red blocks under “Client Authentication.”

Copyright © Packet Passers 2025