Last updated on November 16th, 2022 at 05:12 pm
The Palo Alto Networks Next-Generation Firewall (NGFW) supports DNS Proxy. When you configure the firewall as a DNS proxy, it acts as an intermediary between hosts and DNS server(s) by resolving queries from its DNS cache or forwarding queries to other DNS servers. Basically, the firewall acts as a man in the middle for DNS requests.
Definition of proxy:
• The agency, function, or office of a deputy who acts as a substitute for another
• Authority or power to act for another
Using the firewall to proxy DNS requests provides the ability to control these requests and provide an additional layer of security. Controlling the DNS requests is a primary feature of DNS Proxy in which one or more domain names to which the firewall compares incoming FQDNs and can direct the DNS request accordingly. If the FQDN matches one of the domains in the rule, the firewall forwards the query to the Primary or Secondary DNS server specified for this proxy.
In this example, we have the network (zone) Isolated, which primarily uses the Internet and needs limited access to another internal network. With DNS Proxy, the firewall acts as a DNS server, so hosts on this network make their DNS requests to the firewall interface, in this example, 192.168.99.1.
In the diagram below, we have the Isolated network with hosts who primarily use the Internet. Also, on the firewall, there is the Internet and Servers zone. The Internet zone is apparent, and the Servers zone is the network to which the Isolated hosts access an FTP server.

Let’s review how DNS requests work with DNS Proxy
When a host in the Isolated zone (192.168.99.0/24) makes a DNS request for sample.aws.com, the request is sent to the firewall interface (192.168.99.1). The firewall sends the request on behalf of the host to the configured DNS server, 8.8.8.8. We’ll review this configuration in the following sections. The reply is sent to the firewall, which replies to the host with the resolved IP address.

Once the host has a resolution, the host sends traffic to the server and, in our example HTTPS (SSL) to sample.aws.com. This, of course, is based on a Security Policy allowing the traffic. In another section, I have an example of the Security Policies based on the examples in this article.

Now, this is where DNS Proxy serves a beneficial purpose while maintaining DNS security. If a host in the Isolated zone needs access to a host in another zone and needs the name resolution of that host, DNS Proxy can send a request to a specified DNS server for a specific domain. In this example, the host in the Isolated zone needs access to ftp.example.com.
When the host in the Isolated zone makes a DNS request, for ftp.example.com, the request is sent to the firewall interface (192.168.99.1). The firewall sends the request on behalf of the host to the configured DNS server. For hosts in the example.com domain, the DNS requests are sent to 192.168.10.20. We’ll review this configuration in the following sections. The reply is sent to the firewall, which then replies to the host with the resolved IP address.
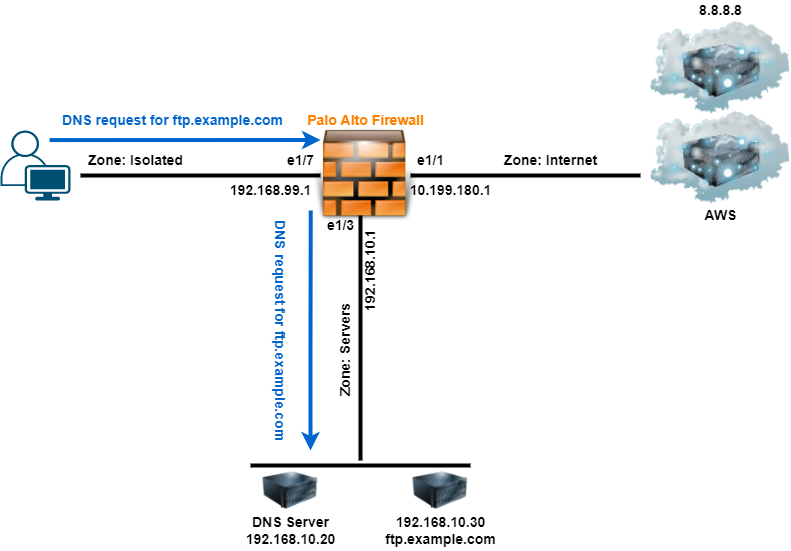
Once the host has the name resolution, the host sends traffic to the server and, in our example FTP to ftp.example.com. This, of course, is based on a Security Policy allowing the traffic. In another section, I have an example of the Security Policies based on the examples in this article.

Let’s Review the Firewall Configuration
Here is the configuration of the firewall interface for the Isolated zone.

For the Isolated zone, the firewall is the DHCP Server (Network>DHCP) which the Lease settings are basic.

Here are the DHCP Server Options settings. Notice, the Primary DNS server is the firewall’s e1/7 interface IP address. This makes the firewall the DNS server for hosts in the (Isolated) zone.

The DNS Proxy settings (Networks>DNS Proxy) are where we specify which DNS servers to use for hosts on the specified interface, in our example e1/7 which is the Isolated zone. The Name field is any name you wish and only has meaning to the admin. Under the Interface section, specify the interface this configuration will apply. You can apply this to multiple interfaces if needed.
The Primary and Secondary are the DNS servers used by default for name resolution. In our example, the hosts in the Isolated zone primarily use the Internet, so we are using Google’s DNS servers. In our example in Figure 2, when a host requests resolution for sample.aws.com, the firewall sends the request to 8.8.8.8 or 8.8.4.4.
The DNS Proxy Rules section specifies where the firewall sends DNS requests based on the domain name. If this section is left blank, all DNS requests are sent to the Primary or Secondary DNS servers, 8.8.8.8 or 8.8.4.4.
In this example, requests to resolve hosts in the example.com domain, the firewall sends DNS requests to 192.168.10.20 or 192.168.10.21. In our example in Figure 4, when a host requests resolution for ftp.example.com, the firewall sends the request to either of the two specified DNS servers. We only have one domain specified with this example, but multiple domains can be used.

By default, same zone (intrazone-default) traffic is allowed. However, if there’s a “deny” security policy for the zone, as in our example below, a security rule is required allowing DNS traffic. The Security Policy should allow DNS traffic to the firewall interface, and in our example, 192.168.99.1.
The Security Policies below allow the traffic as outlined in this article.

Reference Links:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClFcCAK
Copyright © Packet Passers 2025


