Last updated on February 19th, 2026 at 07:28 am
My first experience with VPN was in early 2000, with the Fort Knox Policy Router. Since then, I have configured user and site-to-site (S2S) VPNs with WatchGuard, SonicWall, Cisco PIX & ASA, and Palo Alto Networks. I, and anyone working with VPN, have seen the encryption algorithms change over time. Also, coordinating the settings on both sides is challenging with site-to-site VPNs, mainly when another party controls the VPN at the other end.
Over the years, as I have worked with S2S VPNs with multiple vendors, situations, and companies, I’ve maintained a VPN Request Form. The form is based on experience and other request forms, and I have updated with the latest algorithms as they become available. The form is available for download (link below), and below I provide steps to protect it if sent to another party.
As I updated the form with the latest algorithms, I took the opportunity to research them. This post is not about the details of the algorithms, but if you want to know more and need help falling asleep, you can find more information with the Request For Comment (RFC) documents.
The encryption algorithms have come a long way, for example, Data Encryption Standard throughout the years, based on the recommended use order:
DES 56 bit > 168 bit (3DES) > 128 bit AES GCM > 256 bit AES GCM
I won’t explain how to create an S2S VPN in this post as there are many other resources. My goal is to help you with the available algorithms and the trends in use today. The charts below are based on many resources which describe the available options and pros and cons. I’m not promoting any specific configuration, just summarizing what I have found that is current, is used, and based on articles on specific use, for example, an S2S with another company or government. When choosing cryptographic options for an S2S VPN, company, government, compliance, and even legal requirements must be considered.

The graphic above I made is based on what I explained in the previous paragraph. When choosing VPN options, keep in mind that the newer ((or Next Generation Encryption (NGE)) algorithms do use more resources (CPU, memory) than the previous algorithms. On the other side, newer firewalls obviously have more CPU and memory than older models. When creating an S2S VPN, I consider what data traverses the VPN, the other side (gov, another office, vendor), and compliance. For example, I don’t use IKE: Group 20 SHA512 AES-256-gcm, IPsec: Groups 20 SHA512 AES256-gcm for every S2S VPN.
I’m fortunate to work with the latest generation firewalls, mainly Palo Alto Networks, but given the number of VPNs, using those setting for all would consume too many resources. Though, what has worked well in many environments, we use a firewall pair (HA pair) for S2S and user VPNs and another pair as an Internet firewall. This is based on budget, of course.
This graphic is for IKE (Phase 1) VPNs and again based on research on the subject. These recommendations are based on other resources, so make your best judgment.

There are SSL VPNs and their encryption options, and I did not cover those in this post, but I will in another.
I hope this has been helpful, and again below is the VPN Request form and information.
VPN Request Form
The VPN Request Form is formatted for Word 2010 or better. It contains the latest algorithms but may not be compatible with all firewall vendors or versions. Negotiating these algorithms and settings is one of the challenges with an S2S VPN. If you want to remove or change the drop-down options in this form, you need to use Developer Mode in Word.
NOTE: To download the form, right-click on the button below and select “Save Link As” and choose where to save the document.
If you want to protect the form after filling in your information and sending it to another party, follow the steps below. This will protect the document but only allow the other party to fill in the form sections.
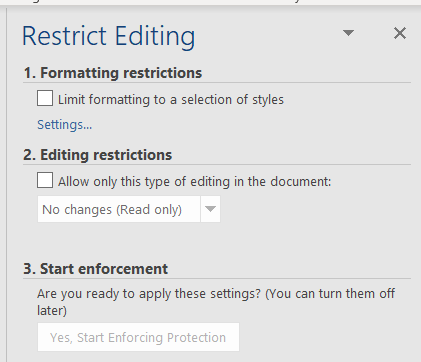
In Word go to File > Info > Protect Document > Restrict Editing
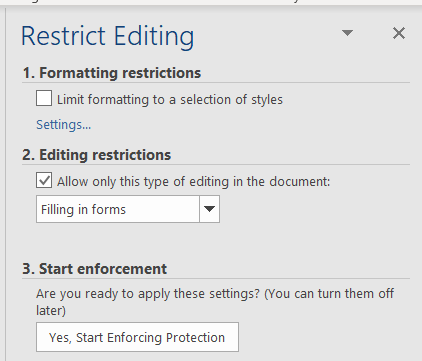
Under 2. Editing restrictions, check the box Allow only this type of editing in the document.
Then select Filling in forms.
Click the Yes, Start Enforcing Protection button.
After clicking the button you will be asked for a password to protect the document.
Note: There is no password recovery for the document so retain the password in a safe place.
Reference links:
https://tools.cisco.com/security/center/resources/next_generation_cryptography
Copyright © Packet Passers 2025
Palo Alto Networks IPSec Resource List:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Clh5CAC
Palo Alto Networks How to Configure IPSec VPN:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClGkCAK
Palo Alto Networks IPSec Crypto Options:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClYtCAK
Palo Alto Networks Documentation IPSec Crypto Profiles:
https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/vpns/set-up-site-to-site-vpn/define-cryptographic-profiles/define-ipsec-crypto-profiles.html
Cisco Next-Generation Cryptography:
https://tools.cisco.com/security/center/resources/next_generation_cryptography
NIST Guide to IPSec VPNs:
https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-77.pdf
Very good article on selecting the best AES cipher:
https://isuruka.medium.com/selecting-the-best-aes-block-cipher-mode-aes-gcm-vs-aes-cbc-ee3ebae173c