Last updated on February 19th, 2026 at 07:27 am
A Palo Alto Networks firewall configured as a GlobalProtect Portal or Gateway will, by default, display a page to download the GlobalProtect client. As with anything in life, this can be a good or bad thing.
This feature has created some downsides. If enabled, your firewall becomes a repository to which anyone can download the GlobalProtect (GP) client. Also, it provides a web page to be exploited. One example is that employees can download and install the GP client to a personal computer and then use their credentials to connect to the VPN from that personal computer instead of the corporate-provided laptop or desktop. Or connect from both at the same time.
The upside of this page is allowing users to download the GP client for installation, which is very convenient. Though today with much compliance, this page should be disabled or access to it blocked. If possible, the installation of the GP client should be managed with a Mobile Device Manager (MDM) or similar management platform.
This GP download page can be directly accessed (up to version 10.1) using the following links. The name vpn.example.com would be replaced with the production GP page.
https://vpn.example.com/global-protect/getsoftwarepage.esp
https://vpn.example.com/global-protect/getmsi.esp

Caution: Block Access to the Download Pages
IMPORTANT: If a manual or transparent upgrade is allowed in the GP App configuration on the firewall and these links are blocked, the upgrade will fail.
Note the important message above. If you have the firewall configured (manual or transparent) to upgrade the GP client when a user connects and these links are blocked, the upgrade will fail. In testing, when I had this enabled to upgrade to a new GP client version activated on the firewall, the upgrade failed even though the user received a prompt that an upgrade would occur.
Create URL Category & Security Policy
We’ll start with the GUI to create the needed URL Category and Security Policy. Further down, I have the text to do the same at the CLI.
Let’s start with the URL Category we need.
Objects>Custom Objects>URL Category and click Add
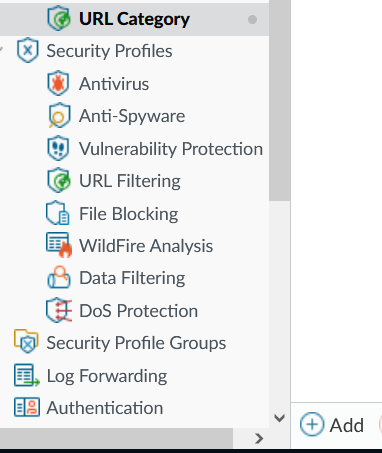
Give the category a name; in this example, we use block-gp-sw-page.
For Type, select URL List.
In SITES, add the two URLs but remember to use those which pertain to your environment. Also, note the asterisk at the start of the URL. We do this in case we have multiple DNS record names, for example, vpn.example.com or gateway.example.com. Using the wildcard (*), we will block all *.example.com. If you want to be specific, you can remove the wildcard (*) and use the specific name, for example, vpn.example.com.
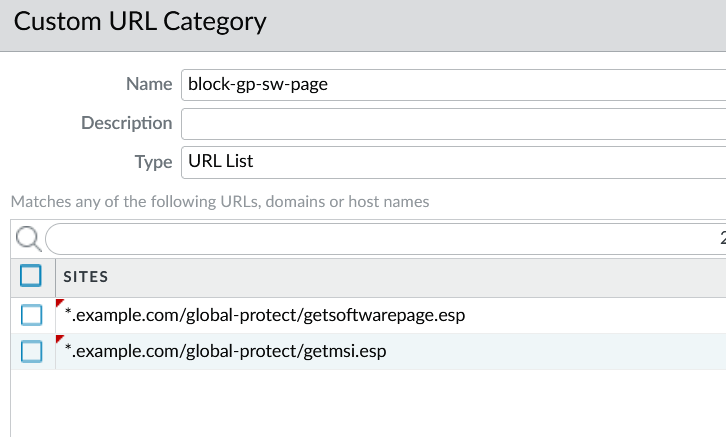
Click OK in the Custom URL Category window.
The Security Policy
Now we can create the Security Policy to block access to the GP client download page.
Go to Policies>Security and click Add.
Give the policy a name; in our example, we use block-gp-sw-page.
Rule Type: universal
The Description is optional, but I always use one, especially I add my name, date, and if there is a ticket or some request number requesting this Security Policy.
On the Source tab, the Source Zone is the Internet side zone and in our example is Internet.
In the Destination tab, the Destination zone is the same as the source, and our example is Internet.
In the Application tab, the default of Any for applications.
Then in the Service/URL Category tab, application-default can be used or any. For URL Category, click Add. Begin typing the name of the URL Category we created previously. Once the name is displayed, click on it to select.
In the Actions tab, in Action Setting for Action, select Deny, and if you want to monitor traffic hitting this policy, under Log Setting, select Log at Session End. In most cases, this policy should be at the top of the Security Policy list.
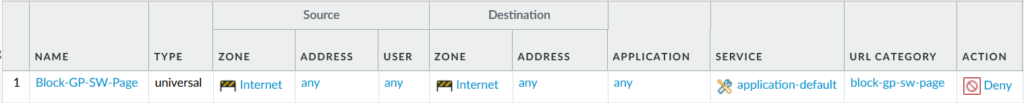
Once you review this configuration, Commit the changes.
Post Commit Testing
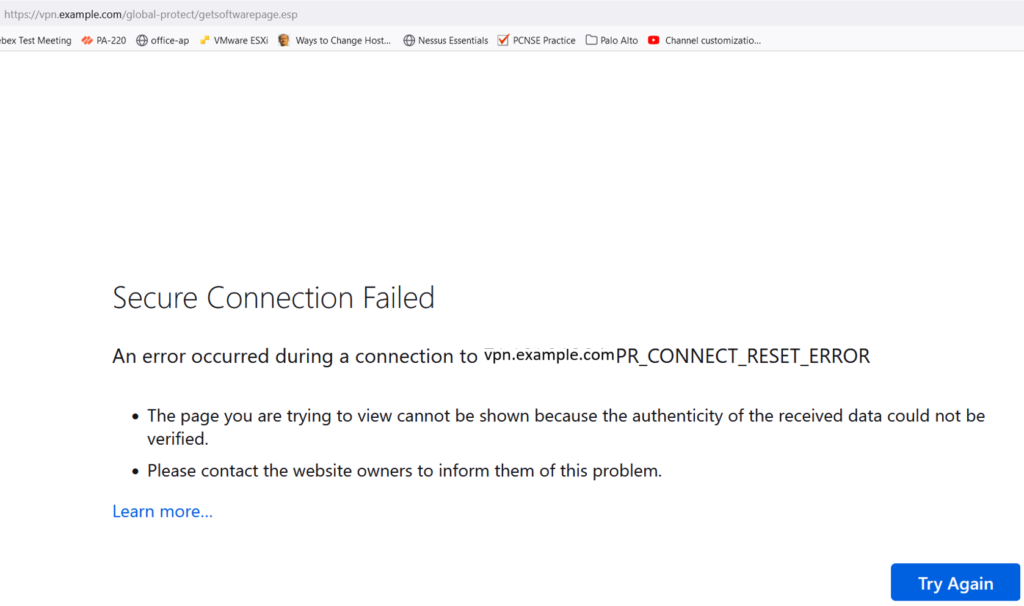
Once the commit is done and successful, the URL links should be tested from an outside source.
From our example, https://vpn.example.com/global-protect/getsoftwarepage.esp should no longer be available. Depending on the browser, either a “This site can’t be reached” or a “Secure Connection Failed” message will display.
CLI Version
Here is the CLI version of this configuration.
set cli config-output-format set
configure
set profiles custom-url-category block-gp-sw-page type “URL List”
set profiles custom-url-category block-gp-sw-page list [ *.example.com/global-protect/getsoftwarepage.esp *.example.com/global-protect/getmsi.esp ]
set rulebase security rules Block-GP-SW-Page to Internet
set rulebase security rules Block-GP-SW-Page from Internet
set rulebase security rules Block-GP-SW-Page source any
set rulebase security rules Block-GP-SW-Page destination any
set rulebase security rules Block-GP-SW-Page source-user any
set rulebase security rules Block-GP-SW-Page category block-gp-sw-page
set rulebase security rules Block-GP-SW-Page application any
set rulebase security rules Block-GP-SW-Page service application-default
set rulebase security rules Block-GP-SW-Page hip-profiles any
set rulebase security rules Block-GP-SW-Page action deny
set rulebase security rules Block-GP-SW-Page rule-type universal
set rulebase security rules Block-GP-SW-Page description “Block access to GlobalProtect software download page”
set rulebase security rules Block-GP-SW-Page disabled no
move rulebase security rules Block-GP-SW-Page top
Conclusion
As of the writing of this article, on some of the PAN Live Community posts, disabling the download page via a GUI option has been a requested feature; see Resources below.
As noted previously, there are consequences to disabling the download page, but as mentioned earlier, there are benefits to disabling this page. In my experience and that of others, compliance has requested this page be disabled, and with many, the PAN VPN client is managed with an endpoint (mobile device manager) utility.
Resources (some of the PAN links may require an account to access):
Copyright © Packet Passers 2025